In today’s digital world, code strings like b0bn4f6wyq play a crucial role in ensuring security and privacy. These seemingly random sequences of alphanumeric characters are used in a variety of contexts, from passwords and API keys to encryption and data integrity checks.
While they may appear cryptic, these strings are often essential in safeguarding sensitive information against unauthorized access and attacks. Understanding the purpose and structure of such codes is vital in navigating modern cybersecurity practices.
In this article, we will explore the different uses and technologies behind code strings. By the end, you’ll gain a clearer understanding of their importance in digital security.
What Is a Code String?
A code string is essentially a sequence of alphanumeric characters that can represent data, identify resources, or serve as keys or hashes in cryptographic processes. For example, b0bn4f6wyq could be a part of a URL shortening service, an API key, a user identifier, or a randomly generated password used for authentication.
Role of Randomized Strings in Security
The randomness and complexity of these strings play an essential role in ensuring system security. Randomized strings, like b0bn4f6wyq, help minimize the risk of unauthorized access or attacks. Their unpredictability makes it nearly impossible for hackers or malicious actors to guess or decipher the correct values.
Understanding the Different Uses of Code Strings
1. Passwords and Authentication
One of the most common uses of alphanumeric strings like b0bn4f6wyq is in authentication systems. Whether used for logging into an account, verifying an identity, or providing access to secure systems, passwords are often designed to be long and complex. Code strings with a mix of letters and numbers increase the security of these systems by making passwords difficult to guess or brute-force.
2. Hashes and Integrity Checks
A hash is a function that takes an input and returns a fixed-size string, which usually appears random. Hashes are widely used in data integrity checks and storing passwords securely. If b0bn4f6wyq were a hash, it would represent the result of a hashing algorithm applied to some original input data. Hashes are commonly used in blockchains, databases, and file storage systems to verify that the data has not been tampered with.
The Technology Behind Code Strings
1. Cryptographic Algorithms
Many code strings are generated using cryptographic algorithms. These algorithms are designed to produce unpredictable results that are computationally difficult to reverse. Common algorithms used to generate these strings include SHA (Secure Hash Algorithms), MD5, and HMAC (Hash-based Message Authentication Code).
The core idea behind these algorithms is to create a fixed-length output that appears random. The input to these algorithms could be anything from a file’s content to a password, but the output will always be a seemingly random string. This ensures that even small changes in the input lead to completely different outputs.
2. Base Encoding Systems
Strings like b0bn4f6wyq may also use encoding schemes such as Base64, Base32, or Base58 to represent binary data in a human-readable format. These encodings are especially useful for representing data in systems that only allow alphanumeric characters, such as URLs and email addresses.
FAQs
1. What is a code string like “b0bn4f6wyq” used for?
Code strings like b0bn4f6wyq are often used in security systems, including passwords, authentication tokens, hashes for data verification, or even shortened URLs.
2. Can I decode the string “b0bn4f6wyq”?
Without knowing the specific encoding or algorithm used, it’s impossible to directly decode such a string. It could be a hash, token, or any randomly generated string.
3. How do I generate secure random code strings?
To generate secure random code strings, you can use a cryptographically secure random number generator (CSPRNG), or you can use libraries in programming languages like Python (secrets module) or JavaScript (crypto module).
4. Is “b0bn4f6wyq” a password?
It’s possible that this string could be used as a password, especially in systems requiring alphanumeric passwords. However, without additional context, it’s difficult to say for sure.
5. What is a hash, and how is it different from a code string?
A hash is the output of a hashing algorithm applied to input data. It’s a one-way transformation, meaning it can’t be reversed to get back to the original data. A code string can be a password, token, or identifier, which may or may not be the result of a hash.
6. Why are random strings like “b0bn4f6wyq” considered secure?
Random strings are considered secure because they are unpredictable, which makes them hard for attackers to guess, especially when combined with algorithms like hashing and encryption.
7. How can I generate a hash from a string like “b0bn4f6wyq”?
You can generate a hash from a string using cryptographic functions such as SHA-256 or MD5. These are commonly available in most programming languages.
8. What is the role of base encoding in generating code strings?
Base encoding systems (like Base64) are used to convert binary data into readable text. They are essential when you need to represent binary data in systems that only support text.
9. How do code strings enhance system security?
Code strings, especially those that are randomized, prevent unauthorized access by being hard to guess or predict. They add an extra layer of security, especially when used as part of multi-factor authentication (MFA).
10. Can a code string like “b0bn4f6wyq” be reused?
In most cases, code strings like authentication tokens or passwords should not be reused to ensure security. Reuse can increase the risk of exposure or compromise.
Conclusion
In summary, b0bn4f6wyq might appear as a simple string of random characters, but its usage is deeply ingrained in a variety of digital security practices. From passwords to hashes and tokens, code strings like these help ensure secure communication, data integrity, and user authentication in today’s interconnected world.
Understanding these cryptographic concepts and their applications is crucial for anyone working with technology or security. As systems become more complex, the need for strong, secure, and unpredictable strings of characters will continue to grow, making them an essential part of our digital landscape.
Whether you encounter a code string like b0bn4f6wyq in your password manager, as part of a cryptographic process, or while interacting with a web service, knowing how these strings function and why they are important will help you better navigate the world of digital security.







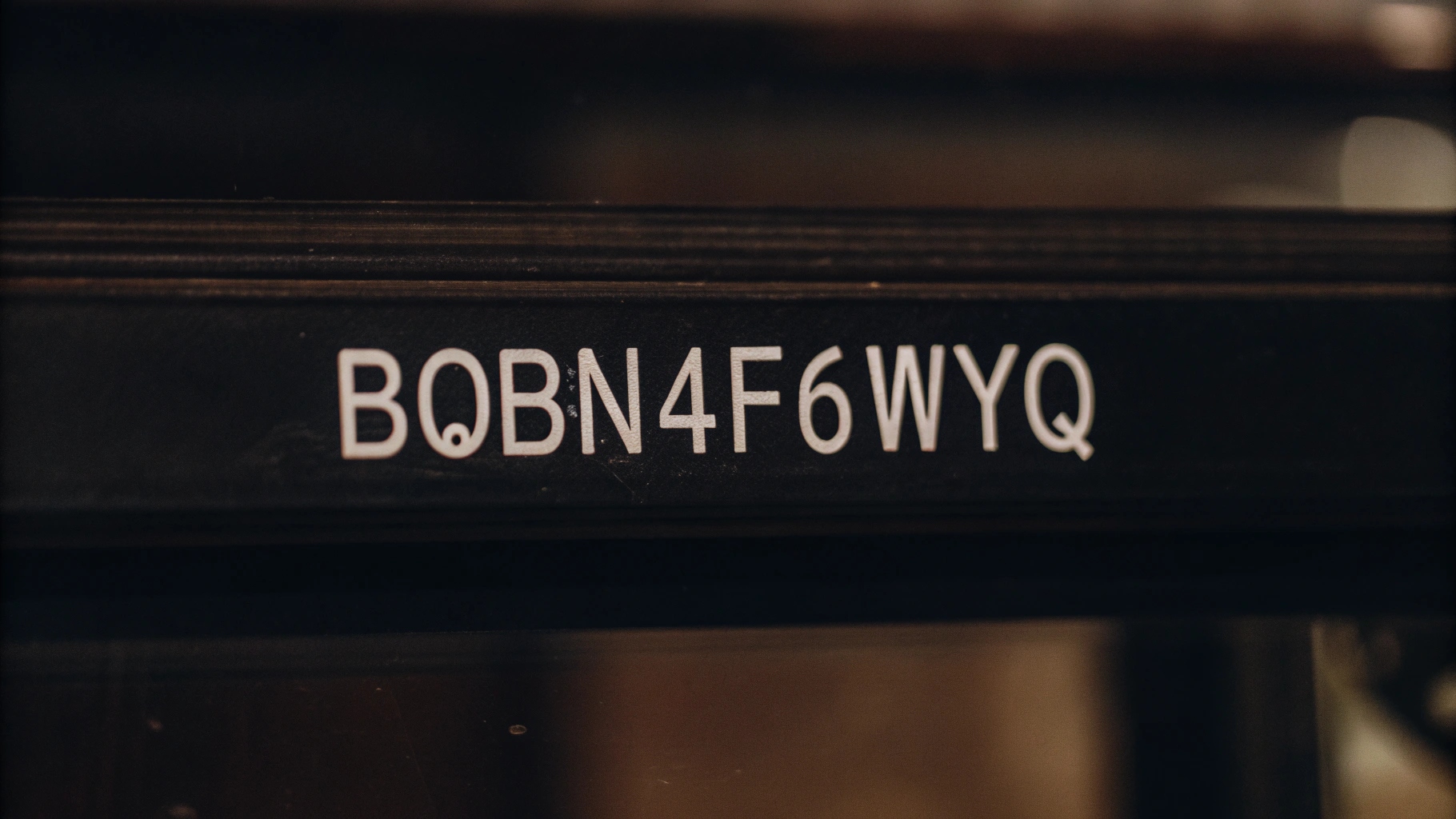







+ There are no comments
Add yours